Meeting management software for board and executive teams
Meetings, decisions, and actions — all in one secure platform
Streamline decision-making, shorten meeting set-up, and securely access everything you need from anywhere.
- Quickly build agendas, and add assignees and collaborators
- Easily record and track discussions — and capture minutes in a template based on the meeting’s agenda
- Instantly assign tasks and track their progress
- Securely access your documents — offline as well as online — and from anywhere
- Discuss decisions, projects, or give feedback via the Sherpany tool before, during, and after meetings

The go-to solution for boards and executives at Europe’s top companies
Does your business suffer from these problems in meetings?
Slow meeting processes and complex regulations
Challenge
- Rigid and time-consuming meeting processes resulting in a high volume of manual administrative work.
- Complicated or dysfunctional distribution of meeting material.
- Secure exchange and management of sensitive information and confidential data.
How we help
- Sherpany allows you to create an entire meeting in only 3 minutes and save up to 40% in meeting preparation time.
- Easy and secure management and distribution of meeting materials.
- Designed to simplify compliance management (e.g. RGPD and FINMA).
Create an entire meeting in only 3 minutes, and save up to 40% in meeting preparation time
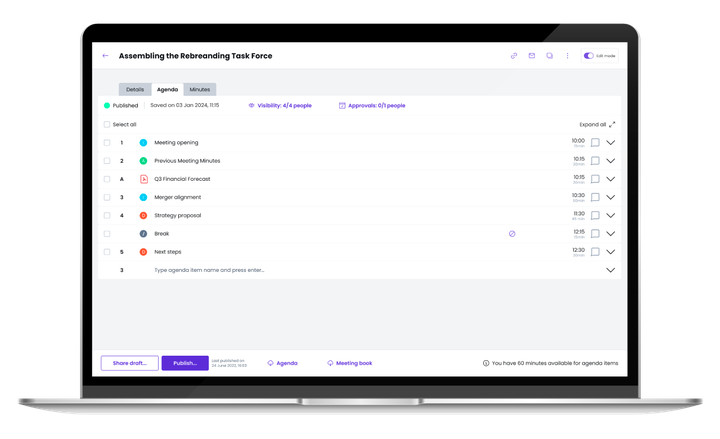
I estimate saving at least 6 hours per week on meeting preparation thanks to Sherpany
Limited collaboration and alignment in meetings
Challenge
- Lack of collaboration and prioritisation in agenda topics prior to meetings.
- Scattered information slowing down discussions and compromising decisions.
- Too many meeting participants slowing down the discussion.
How we help
- Collaborate and align before the meeting through smart agenda features and comments.
- Have all meetings, documents, decisions, and tasks at your fingertips.
- Implement contribution-based participation: Invite key decision-makers to each stand-alone agenda item.
Speed up decision-making by having all meetings, documents, decisions and tasks at your fingertips

With Sherpany information is distributed in a more timely manner, which contributes to streamlining the overall decision-making process
Slow execution of strategy
Challenge
- Lack of a high-level view of the progress of projects and strategic initiatives across teams.
- Missed or delayed business opportunities due to not being able to make quick decisions.
- Lack of control and accountability of tasks and decisions made in meetings.
How we help
- Sherpany gives you an easy and holistic view of projects from initial ideas to implementation.
- Vote remotely while remaining compliant and tracking every decision.
- Clear task assignment and smart meeting minutes means nothing is overlooked.
Maintain oversight of execution with an easy and holistic view of projects, from initial ideas to implementation
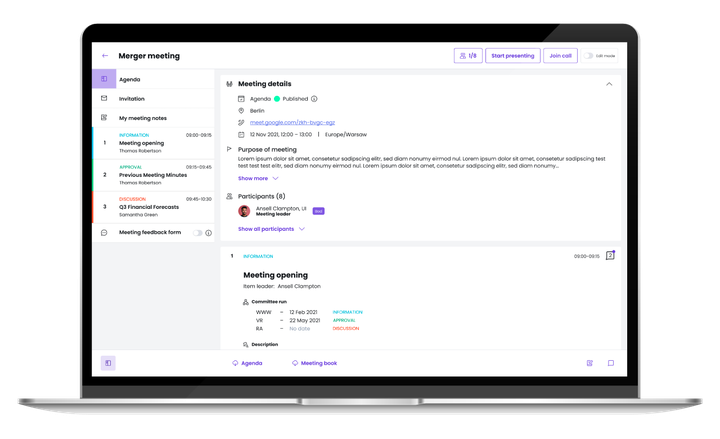
I can consult agendas and documents on all my devices, online or offline, prepare for the meeting, and read the different updates and comments. Moreover, people are always informed even when changes are made at the last minute.
Our partners





Independent Software Vendor

As proud members of the Microsoft ISV Success programme we’re part of a thriving ecosystem that drives innovation and accelerates digital transformation.
Swiss precision and security trusted by leading enterprises
We guarantee that your data is kept safe and compliant with the highest standards
GDPR & FINMA Compliant
ISO 27001 and ISAE 3000 certifications
Unaffected by the US Cloud Act
End-to-end encryption
Access to audit-proof archiving
Remote wiping capability
Granular access control to meeting materials
SCIM provisioning
SAML-based SSO
Sherpany connects with the tools you already use
Your enterprise benefits from a seamless and efficient integration with existing apps and technologies




Our strength in numbers
147,088
meetings held with Sherpany
20,000+
professionals saving time with Sherpany
97.5 %
customer retention rate
Our awards



FAQ
Sherpany's meeting management software is best used by boards and executives from large and midsize companies.
Below are some groups that benefit from using Sherpany:
- Boards of directors
- Board committees
- Supervisory boards
- Executive leadership
Our software helps you increase the productivity of your board and executive meetings throughout the entire meeting lifecycle.
- Before the meeting
Plan and prepare meetings from any location, easily and securely. It's straightforward to build, share, and access the meeting agenda and related documents. Our collaboration features ensure that meeting time remains focussed on topics that require synchronous discussion.
- During the meeting
Sherany's Presenter MOde keeps all meeting participants on the same page during discussions. This enables all attendees to follow the same screen during presentations or when reviewing documents, whether they are present in-person or participating virtually.
- After the meeting
After the meeting, you're able to edit and approve the meeting minutes without having to wait for the next meeting. You're also able to review all decisions and agreed actions and can take them to the next level. Assign tasks and responsibilities to specific stakeholders, track progress, and watch your projects move more quickly.
No, Sherpany is not a videoconference tool. However, you can combine Sherpany with video conferencing tools such as Microsoft Teams, Zoom, or GoToMeeting. Click here to watch a short video on how to set up your remote meetings with Sherpany.
Sherpany gives you and your team numerous opportunities for enhanced collaboration. Some examples include:
- Agenda: The person in charge of organising meetings, which we call Admins, can receive feedback about the agenda and ask Participants to upload relevant documents.
- Preparation: When preparing meetings, users can utilise comments to ask questions or discuss topics in advance with their team or assistant.
- Voting: The meeting participants can use the voting tool to vote on a given subject or simply to consult the poll results.
- Tasks & Decisions: Users can rely on this feature to consult meeting decisions, assign tasks or to follow the progress of a given project.
No. Workstream collaboration tools such as Microsoft Teams are mainly used for company-wide communication and videoconferencing, whereas Sherpany supports the end-to-end process of formal meetings for leadership teams. Therefore, neither tool replaces the other and they can be combined in order to realise your company's full potential.
Yes, you can use Sherpany even without an internet connection if you do it from your iPad, iPhone, Android, or Windows device app.
Sherpany’s pricing model is a monthly fee based on the total number of users, and the customers’ requirements and current meeting processes. Please contact our sales team for more information.
The board plan is the right solution for the meeting management of one board. It includes the functionalities needed to prepare and run board meetings, including:
- Digital Circular Resolution meeting type with Digital Signatures
- Board book for member archiving
- Approval workflows for agenda and minutes
- Document management for secure document exchange with Board members (Library)
- Agenda item permission management to manage conflicts of interest.
The enterprise plan is ideal for the meeting management of large enterprises and/or highly-regulated industries (e.g. banking, insurance, healthcare). It includes unlimited meeting rooms, 24/7/365 support, and enhanced features such as:
- Support for conditional access (IP filtering, whitelisting)
- Pop-ups for all users accessing Sherpany, which can be renewed periodically. Content can be defined by customer, applicable for privacy and customer identifying data disclaimers.
- Preventing copy/paste from PDF documents in Sherpany
- Possibility to upload password-protected PDF files in Sherpany
- Making watermarks always visible on documents uploaded to Sherpany
- Confidential Mode for notifications to avoid sensitive content being shared via email.
After the initial onboarding there are two options to onboard new users to Sherpany:
- Self-service onboarding, where the users can onboard themselves through our standardised onboarding program.
- Individual onboarding with our customer success specialists (at an additional cost).
Sherpany offers several integrations with existing apps and technologies, such as:
- SSO (Single Sign On) / SAML2
- User provisioning
- Microsoft Office 365
- Calendar integration, with the possibility to sync Sherpany meetings in any calendar (Microsoft Outlook 365, Google, etc.)
- Video calling solutions (Microsoft Teams, Cisco Webex, Skype, Google Meet, etc.) for remote meetings
- IFTT
- Box
- Auth0
- Customizable API
- Mobile Device Control
- Microsoft first strategy
Data security is a top priority at Sherpany. As a result, there are several measures in place to:
- Secure your meetings
- Safeguard your data, and
- Assure data privacy.
These include, but are not limited to:
- Two-factor authentication
- Different levels of access to meeting documents
- End-to-end encryption methods
- Compliance with the EU's GDPR, and the security standards outlined by the Swiss Data Protection Regulation.
Please visit our security page to discover all of our security measures.
Once onboard, Sherpany will provide you with the following support options:
- 24/7 support: we give your organisation 24/7* support in English, German, Italian, French, Spanish, and Portuguese. Your users can reach out to us via phone, email or chat. * 24/7 support is included in the Standard and Enterprise plans.
- Review and planning meetings: we conduct consulting meeting sessions where your assigned customer success manager reviews your usage of Sherpany, presents you with new features, and gives you advice on how to further improve your meetings.
- Sherpany Knowledge Center: an online platform where you can find tutorials, our latest updates on features, modules, and best practices.
We are able to onboard a leadership team of 20 members in less than three weeks. However, onboarding can be done faster depending on your availability.
For companies onboarding more than 100 users, we offer an automated onboarding process.
Always. Our support team is available 24/7* so you can reach out to us at any time. On average, our support team answers phone calls within five seconds.
* 24/7 support is included in the Standard and Enterprise plans
Our support is available in English, French, German, Italian, Spanish, and Portuguese.







